Ransomware Recovery Services
Ransomware Recovery Services

Ransomware attacks are a growing problem for organizations of all sizes. The FBI received between 1,500 and 2,700 ransomware complaints in each of the past 5 years, and each instance of ransomware infection can easily result in thousands of dollars of damages.
Datarecovery.com has developed methods to address cyber threats and help ransomware victims restore access to their data. Our ransomware recovery and decryption services utilize proprietary methods and state-of-the-art technologies to limit downtime after an attack — and provide your organization with cybersecurity defenses to protect against future attacks.
Call 1-800-237-4200 today to speak with cybersecurity experts or read on to learn about the recovery process.
Recovery Services: Maintaining Business Continuity
Ransomware refers to any malicious software that blocks access to data by encrypting the victim’s media. The user is presented with ransom demands, which must be paid with Bitcoin or another cryptocurrency.
In most cases, submitting a ransom payment isn’t an effective recovery method for several reasons:
- Paying the ransom may be illegal. Bad actors are often engaged in other criminal activities and based in Russia, China, and other countries under the jurisdiction of the U.S. Office of Foreign Assets Control (OFAC).
- A significant portion of ransom payments do not result in decryption of the original files. By one estimate, paying ransom doesn’t restore data for 25% of victims.
- Paying ransoms can result in reputational damage, and critical systems may be subject to further attacks.
Your organization needs a systematic approach to ransomware recovery. Datarecovery.com can help.
Our experienced professional engineers have decades of combined experience, and have performed successful ransomware recoveries for hundreds of enterprises. Call 1-800-237-4200 to get started.
Comprehensive Strategies for Minimal Downtime
Your ransomware data recovery plan needs to accomplish several key objectives:
- Restore impacted systems by utilizing case-appropriate decryption tools, utilizing backup files, or another method.
- Identify attack vectors and establish the extent of damage.
- Perform incident triage and ransomware analysis to ensure that the data has not been exfiltrated.
- Maintain business operations throughout the disaster recovery process.
- Monitor dark web portals to ensure that data is not resold, publicized, or otherwise compromised.
A holistic approach must employ advanced decryption techniques, extensive threat intelligence, and proactive measures to prevent additional attacks.
Datarecovery.com leverages decades of experience in cybersecurity best practices to provide peace of mind following an attack. Our goal is to provide organizations with the precise support they need to minimize operational downtime. From basic ransomware recovery to advanced penetration (PEN) testing, regular vulnerability assessments and dark web monitoring, we help you restore key systems with minimal disruption — providing the precise services you need for your unique situation.
Ransomware Recovery
Even with regular backup, mission-critical systems may be compromised by modern ransomware variants. Some sophisticated ransomware files are designed to sit on servers for months prior to activation, which increases the likelihood of total encryption — the malware can impact immutable backups along with primary systems.
Our ransomware data recovery strategy follows several general steps:
- An initial assessment identifies the variant and its impact on key systems.
- Containment measures prevent the ransomware from spreading to other systems.
- If possible, decryption is performed using available tools. If no tool is currently available, attempts are made to develop one by analyzing encryption patterns.
- If the decryption process is unsuccessful, alternative options are explored. This may include restoration from older backups and rebuilding the impacted systems.
- Data is returned to the client. A forensic analysis is performed to fix the vulnerabilities that allowed for the attack.
As the world’s leading ransomware recovery provider, we provide high success rates, unmatched expertise, and fast turnaround times — regardless of the ransomware variant, operating system, or other factors. Call 1-800-237-4200 to start building a ransomware recovery plan.
Preventing Ransomware Attacks
Your ransomware strategy should not end with data recovery. Cybercriminals often target organizations multiple times — especially when extortion attempts are successful.
Our cybersecurity experts can help you take the next steps to prevent additional operational disruptions:
- Forensic analysis identifies the attack vector.
- PEN testing finds other vulnerabilities that could be exposed to attackers.
- Employee training limits the effectiveness of social engineering tactics.
We provide as much or as little guidance as your organization needs. Whether you’re running a mid-size business that needs a comprehensive approach or an enterprise with an established cybersecurity strategy, our experts help you fill in the gaps
Ransomware Services: Dark Web Monitoring
Many ransomware groups exercise a two-pronged attack methodology: After extorting victims for ransom payments, they sell exfiltrated data on the dark web. Datarecovery.com provides monitoring services to find exfiltrated data and shut it down. We work with relevant authorities, leveraging our understanding of the cybersecurity landscape to minimize client data exposure.
Ransomware FAQ
What are some examples of ransomware variants?
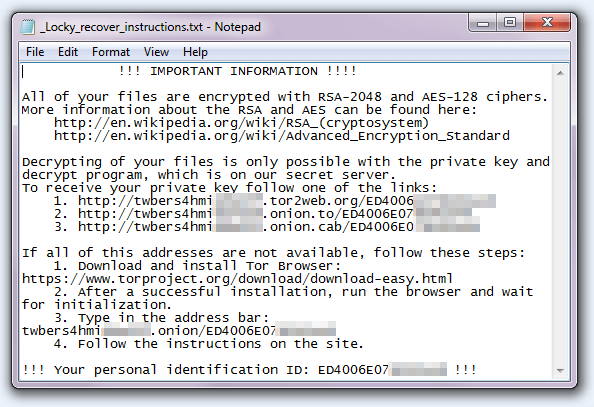 Examples of ransomware include the following and their variants:
Examples of ransomware include the following and their variants:
- SamSam
- Cerber
- Crysis
- CrypMIC
- Locky
- HDDCryptor
- Merry X-Mas
- CryptXXX
- CryptoWall
- CryptoLocker
- TorrentLocker
- KeRanger
- Bart
- Zepto
- Jigsaw
If ransomware encrypts data, is it gone forever?
While many ransomware programs are sophisticated, many are not —ransomware is big business, and many bad actors use fairly basic methodologies.
Ransomware programs use outdated or faulty encryption methods. Additionally, some of the encryption techniques have been broken, and some keys and source code have been recovered (often after the creator is arrested) enabling decryption.
In some cases, encryption is unbreakable. A ransomware data recovery service can still be useful in these cases, as the initial attack vector will need to be identified and closed.
How long does ransomware recovery take?
Turnaround depends on the scale of the infection, the ransomware variant, the nature of the targeted data, and other factors.
In our initial assessment, we provide an estimate of the expected recovery time. Most cases are completed within several days.
Call us at 1-800-237-4200 and ask to speak with a ransomware recovery specialist.
Why shouldn’t I pay a ransomware demand?
Paying ransoms is usually illegal (unless appropriate authorities have been notified). In many cases, public companies must also disclose ransom payments, which can result in reputational damage.
But the primary reasons to avoid payment are simpler: Paying provides an incentive for additional attacks (and doesn’t guarantee data recovery).
What should I do if my systems are infected with ransomware?
Turn off the affected systems. Do not attempt to restore from a backup unless you’re absolutely sure that those systems are free from infection. We strongly recommend working with experienced cybersecurity experts to limit the extent of infection.
Can I negotiate with ransomware attackers?
This is not recommended. While experienced ransomware negotiators exist, they’re typically employed when systems are essential (such as systems related to healthcare or national security).
Bad actors will negotiate in bad faith, and again, paying the ransom should be a last resort.
Does Datarecovery.com offer a ransomware recovery guarantee?
No data recovery company can provide a blanket guarantee for ransomware recovery. Some variants use sophisticated methods that cannot be thwarted without the relevant encryption keys.
However, we base our pricing on the success of the case. Our objective is to provide fast answers in each ransomware incident — and maintain the industry’s highest success rates.
What security gaps lead to ransomware infection?
Most successful attacks use known software vulnerabilities, social engineering tactics, or a combination of the two.
Often, the attackers writing the ransom note are not the people who created the malicious software: Ransomware is often sold by cybercriminal groups to other bad actors. This creates opportunities for recovery engineers — the actual attackers may be unfamiliar with the software they’re using or its intended deployment techniques.
I have a backup. Why would I need a ransomware recovery service?
Ransomware experts can help you close the vulnerabilities that caused the initial infection. We may also help you prevent long-term damage to key systems by ensuring that the backups are implemented correctly.
Datarecovery.com can help you recover from any ransomware attack and develop your initial response plan. Call 1-800-237-4200 or submit a case online to start your initial analysis.
