WannaCrypt ransomware (also known as WannaCry and WanaCrpt0r 2.0) is the latest malware to make headlines by infecting over 250,000 computers in at least 150 countries around the world. Prominent victims include FedEx, Britain’s National Health System, Nissan, and telecom giant Telefónica.
If you have a WannaCrypt infection, immediately shut down the infected device. Call Datarecovery.com at 1-800-237-4200 to discuss your case with a ransomware expert.
What is WannaCrypt Ransomware (And How Does It Work)?
WannaCrypt is a type of crypto-ransomware, a type of malware that encrypts a victim’s files so that they are inaccessible. The attackers then demand a ransom in return for a decryption key.
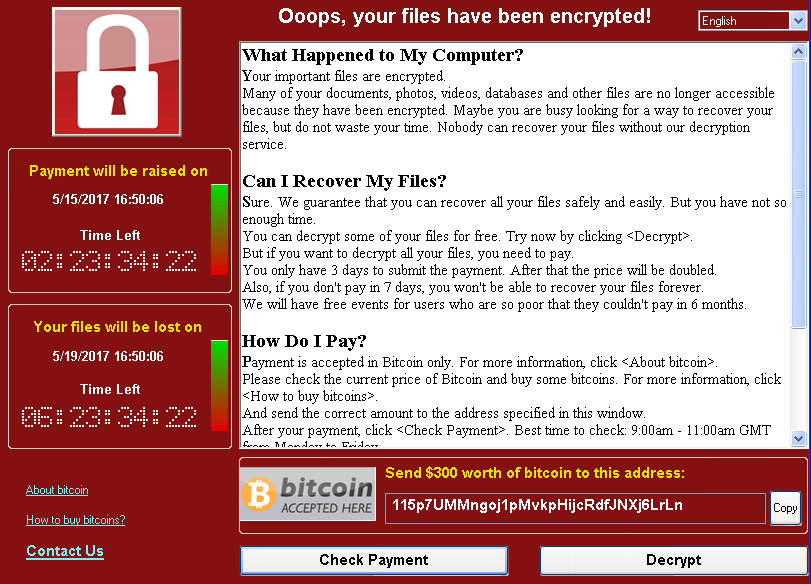
WannaCrypt message. c/o Engadget.
What sets WannaCrypt apart from other ransomware is its unique ability to spread across networks. Likely by using an exploit developed by the U.S. National Security Agency (NSA), WannaCrypt can spread through a network to other machines that have an unpatched Windows operating system.
This was particularly devastating for networks using unsupported operating systems like Windows XP, because there were no patches available. Many companies use older operating systems in order to keep software that is incompatible with newer systems.
Microsoft has now created patches for Windows XP, Windows 8, and Windows Server 2003 in direct response to the WannaCrypt epidemic, despite the fact that the company hasn’t officially supported XP or 2003 for years.
This response helps to underline the severity of the problem; the WannaCrypt attack is easily one of the largest ransomware attacks in history.
Notable features of WannaCrypt Ransomware Include:
- WannaCrypt spreads to unpatched computers in the same network as infected computer.
- It demands a $300 to $600 initial ransom, paid in bitcoin. This amount may increase over time.
- The program has spread to at least 150 countries.
- Prominent victims include NHS, Telefonica, Renault, and FedEx.
- WannaCrypt was temporarily stopped, but new variants are already active.
- Attackers have likely collected over $56,000 in ransom money.
- About 200,000 computers have been infected by WannaCrypt and its variants, but the number is growing rapidly.
- The original version of WannaCrypt uses 2048-bit AES encryption.
Currently, we believe that WannaCrypt uses two NSA exploits, codenamed ETERNALBLUE and DOUBLEPULSAR. These exploits target the Windows Server Message Block (SMB) version 1 file sharing protocol. Recent Windows updates prevent these protocol from being exploited, but many computer systems haven’t received recent updates; as such, the ransomware moves very quickly in some networks.
The spread of WannaCrypt was temporarily halted when a security expert with the Twitter handle Malware Tech registered a domain name he noticed in the ransomware’s code. He intended to use the domain to analyze the infections, but it inadvertently worked as a kill switch and stopped the spread of the malware. Essentially, the program prompts a command & control server at the domain name in question; when it stopped receiving a response, it stopped spreading.
This prevented many infections, but researchers have already spotted new variants of the malware without the so-called “kill switch.” The original version of the worm was not proxy-aware, and therefore, the kill switch wouldn’t work for networks on proxies.
Authorities are searching for the creators of the ransomware; in past cases, when institutions such as the FBI are able to apprehend the writers of malicious ransomware programs, the keys are quickly released. This allows users to restore their data without paying the ransom.
However, there is no guarantee that authorities are close to arrests—or that they’re anywhere close.
How Does WannaCrypt Ransomware Infect My System?
Experts believe that WannaCrypt initially infected computers through a phishing email or a network vulnerability. An NHS employee claimed that a spam email infected the first computer at a Lancashire, England location.
Once WannaCrypt infects a single machine on a network, it can spread to others that do not have the critical patch. It can spread through LAN, so we recommend disconnecting Ethernet before powering on any computer that might be infected.
Users should also apply the newest security patches, as this provides protection from other computers infected with the ransomware. However, the ransomware can still infect a patched computer through the traditional means of malicious email attachments.
Can I Disable or Remove WannaCrypt Ransomware Encyption?
Currently, there is no WannaCrypt decrypter available without paying the ransom. As with all ransomware, the best defense is to prevent infection in the first place. The most critical step for this fast-moving malware is to update your Windows operating system.
Datarecovery.com is investigating workarounds, but because WannaCrypt uses an operational algorithm, some files may be recoverable with traditional methods. The software makes an encrypted copy of each file, then deletes the original; in some cases, we’re able to recover the original file, although with this method, there’s virtually no possibility of a full recovery.
For large files on a network, our specialists may also be able to limit or reduce ransoms. In any case, fast treatment is absolutely essential, especially when WannaCrypt ransomware infects an entire network.
To begin recovering files from a WannaCrypt infection or to learn more, call 1-800-237-4200 and ask to speak to a ransomware specialist.





