 If you had to use one word to describe ransomware in 2016, that word would have to be proliferation. The number of attacks increased, tactics varied, malware variants multiplied, and ransoms grew.
If you had to use one word to describe ransomware in 2016, that word would have to be proliferation. The number of attacks increased, tactics varied, malware variants multiplied, and ransoms grew.
Several high-profile targets were hit causing headaches for the victims and grabbing headlines for the attackers. It was a year of great experimentation for assailants, and businesses and consumers paid a heavy price. To protect against digital threats in 2017, tech professionals should look back on how ransomware spread in 2016 — and why that spread signals an insidious new era in malware propagation.
Why Ransomware Was a Major Threat in 2016
Ransomware is a type of malware that encrypts a computer’s files so that the owner cannot read them. The attackers demand a ransom in return for a decryption key or decryptor software, and users cannot access their files without this key. Decryption is virtually impossible.
Computer users unwittingly install ransomware when they click on a link or an attachment in a phishing email. After the ransomware installs on the computer and encrypts all possible files, a ransom note opens and explains the situation to the victim. The note directs the victim to pay a ransom in bitcoins in exchange for a decryption key.
What’s New in Ransomware in 2016?
Statistics on ransomware are difficult to come by because many victims don’t report the crime. However, what we know is alarming. In 2016, ransomware attacks rose by 6,000 percent, according to IBM. The vast majority of these attacks were not successful because people are wising up about clicking on unknown links.
In addition to a massive increase in phishing campaigns, there has also been a 600 percent increase in the development of ransomware families since December of 2015. This indicates more attackers are getting into the ransomware market, and it means that efforts to crack encryption will be spread thin.
The Major Players of 2016 Ransomware
Locky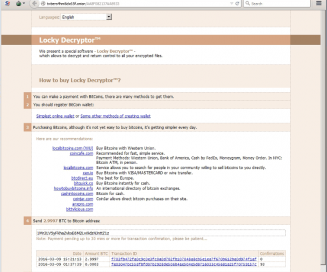 was the biggest name in ransomware in 2016 thanks to a brilliant, if sinister, social engineering technique. The ransomware was sent in an email attachment to millions of people. The MS Word attachment was disguised as an invoice that, when opened, showed only gibberish along with “Enable macro if data encoding is incorrect.” If the user enabled macros, the process started that would ultimately lead to the encryption of the victim’s files.
was the biggest name in ransomware in 2016 thanks to a brilliant, if sinister, social engineering technique. The ransomware was sent in an email attachment to millions of people. The MS Word attachment was disguised as an invoice that, when opened, showed only gibberish along with “Enable macro if data encoding is incorrect.” If the user enabled macros, the process started that would ultimately lead to the encryption of the victim’s files.
KeRanger made a name for itself by infecting around 7,000 Mac users before being shut down. It was the first known instance of Macs being affected by ransomware. Various ransomware has affected Android users in the past, but Kaspersky reports that the beginning of 2016 saw a tremendous spike in attacks on Android-based devices.
Attacking Big Businesses is a Big Business
The dangers of ransomware to large organizations were made clear by attacks on high-profile targets. These targets were often given astronomical ransom amounts due to their perceived ability to pay more.
On Black Friday, ransomware infected the computers of the San Francisco Municipal Transportation Agency, leading to free rides for passengers since ticketing kiosks weren’t functioning. A partial list of major institutions that paid attackers for decryption keys includes the following (see links for details):
- Hollywood Presbyterian Medical Center

- The University of Calgary
- The Melrose Police Department
- Carleton University
These organizations either confessed to paying ransoms or were outed as ransomware victims. We believe that thousands of other businesses were likely quietly victimized. That’s part of the threat; ransomware victims rarely publicize they have weaknesses in their IT systems, for obvious reasons. However, the focus on larger businesses and public organizations is unlikely to drop off in 2017.
As the malware industry becomes more lucrative, we believe that it’s only a matter of time before well-designed ransomware affects major businesses. A ransomware programmer (or, more likely, a team of programmers) might even target government offices, and the ransom might not be monetary. No system is completely safe, and by definition, larger networks become more susceptible to the threat.
Ransomware-as-a-Service
Ransomware developers are nothing if not entrepreneurial. After all, they’ve turned a phishing scheme into a billion dollar industry; the fact that they are exploring the software-as-a-service (SaaS) model shouldn’t come as a surprise.
Some ransomware developers are now selling their creations to people who want in on the profits, but don’t have the necessary skill set. TrendMicro reports that buyers can purchase a lifetime license to a particular kind of ransomware called Stampado for just $39.
The buyers then send out the phishing emails and attempt to extort victims while the developers can focus on creating malware and collecting money. This disturbing development indicates that a far larger number of criminals will be able to launch ransomware attacks. It also portends that different aspects of ransomware attacks will become specializations, which can only mean the attacks will be more sophisticated in the future.
Defending Against or Removing Ransomware
Removing ransomware is a difficult process in most circumstances. Individuals and businesses can protect themselves with the following simple actions:
- Update software regularly so that vulnerabilities are patched as quickly as possible.
- Back up data regularly. Ask yourself the question, “If I lost everything on my computer right now, could I easily restore the information?”
- Don’t click on unknown links or attachments.
In the past, spotting phishing emails has been fairly easy for those with an even mildly informed eye. Ransomware attackers are becoming cleverer by disguising their malware as receipts, tracking information, or other seemingly legitimate documents. Just remember, if you don’t click on it, you can’t be infected.
What’s Next for Ransomware in 2017?
As mentioned above, determining that a message is spam is generally not that difficult, even when the message comes from a contact. If the new ransomware called Popcorn Time takes off, that could change in a big way.
Researchers at MalwareHunterTeam discovered code for this new ransomware on the dark web. When Popcorn Time infects a computer and encrypts its files, the ransom note offers a “nasty way” to receive the decryption key. If a victim can infect two other people who eventually pay, then the original victim will receive a decryption key.
Compelling people to purposely target their own contacts for infection could be an extremely effective way of spreading malware. Time will tell if victims will be unscrupulous enough to spread the misery to avoid paying the ransom.
More on 2017 ransomware expectations here.
Looking Ahead
Everyone from the U.S. government to casual web surfers has been swept up in this new world of cyber sabotage. Staying informed and taking the necessary precautions will help you stay out of harm’s way. As dire as the situation may seem, computer users who back up their files, update their software, and stay away from suspicious links and attachments can rest easy.





