Ransomware grew into a billion-dollar industry in 2016, and from all appearances, it’s just getting started. The malware’s demonstrated ability to bring in money with little upfront investment, along with the outsourcing of the technical work through Ransomware-as-a-Service (RaaS), will likely bring in more organized and sophisticated attackers.
Here’s what to expect from ransomware in the coming year.
- Crypto-ransomware will continue to squeeze locker-style ransomware out of the market.
- RaaS will promote division of labor between developers and attackers.
- This division of labor will lead to more sophisticated coding and methods of attack.
- Attackers will target the Internet of Things if they can make it profitable.
Crypto-Ransomware Will Dominate Locker-Style
There are two basic types of ransomware–locker-style and crypto-ransomware. Since 2015, crypto-ransomware has steadily been squeezing locker ransomware out of the market.
Locker-style malware locks a victim’s computer screen, so that victims can’t use their computer or device. However, if a victim manages to remove the ransomware, they will then have their files back.
Crypto-ransomware encrypts a victim’s files so that they are unreadable. Deleting the ransomware still leaves files inaccessible. That makes recovering files from crypto-ransomware an extremely difficult process.
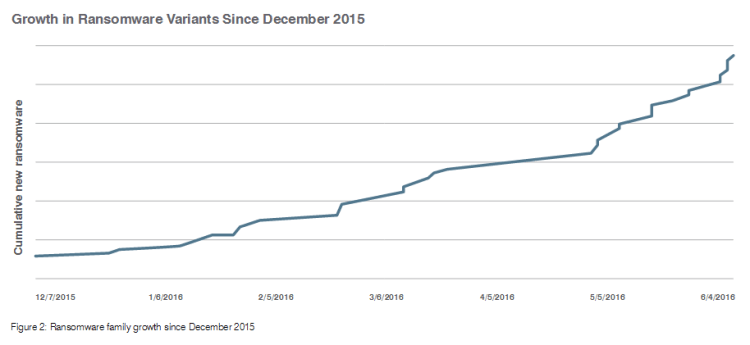
The dominance of crypto-ransomware looks to continue in 2017. The strength of encryption gives the attackers a great advantage. As cybercriminals invent new families of ransomware and new variants of already-cracked ransomware, efforts to decrypt files without paying a ransom will be stretched thin.
Ransomware-as-a-Service
A relatively new development in this criminal industry is RaaS. Developers of ransomware can sell subscriptions to their code to people who don’t have the technical skills to make their own malware. The buyer can then attempt to infect people with the ransomware while the developer receives a monthly payment and/or a percentage of profits.
If someone falls victim to ransomware, they probably don’t care about the organizational structure of the group that infected their computer. However, this division of labor is important because it allows computer scientists to spend their time developing malicious code while criminals figure out how to infect victims. The potential for sophistication in attacks will grow with this specialization.
Spear-Phishing Will Increase Success Rates
Phishing is the most common way to launch ransomware attacks. The attackers send out thousands of emails with malware in an attachment or a link. A very small percentage of these emails are opened, with anti-virus software screening out many of them. Only five percent of people who open a phishing email download the attachment or click on the link.
 While phishing still yields plenty of victims, campaigns require thousands of email addresses to make money from the small percentage of successes. Spear-phishing could change all of that.
While phishing still yields plenty of victims, campaigns require thousands of email addresses to make money from the small percentage of successes. Spear-phishing could change all of that.
Spear-phishing refers to targeted phishing emails. Attackers still hide the malware in an attachment or link, in addition to tailoring the message to the victim. For instance, an attacker could write an email to a college professor with an attachment called “late assignment.” The professor, fearing that he might miss an important assignment from a student, would download the attachment, which would start the process of infecting his computer.
Spear phishing has two great benefits for the attacker. One, the personalized attack makes it more likely to be successful, and two, the attackers can aim for more prominent targets.
Ransoms, Added Costs, and the Price of Lost Information
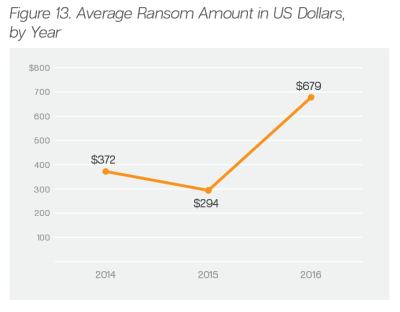 The average ransom rose from $294 to $679 from the end of 2015 to the middle of 2016. As cybercriminals figure out who is willing to pay what, they will likely begin to refine their asking prices to segment their victim population and maximize profits.
The average ransom rose from $294 to $679 from the end of 2015 to the middle of 2016. As cybercriminals figure out who is willing to pay what, they will likely begin to refine their asking prices to segment their victim population and maximize profits.
One highly successful ransomware variant, CryptoWall 3.0, raised $325 million in ransom payments according to a CyberThreat Alliance report. If that sounds like a lot, imagine what the business that paid stood to lose from the attacks.
Even if a victimized business finds a decryption tool for their ransomware and it works perfectly, the process requires time that the business could spend on more profitable activities. In the worst case scenario, a business could pay the ransom and still not get their data back.
“The Internet of Things” And Hacking
An emerging concern of security analysts is the vulnerability of the Internet of Things (IoT). IoT refers to the interconnection of common objects through the internet. For instance, when you set your DVR to tape a show through your mobile device, you’re using the IoT. An internet-enabled pacemaker would be another example and perhaps a more attractive attractive targets for attackers.
Security experts warn that IoT devices are high security risks because many devices use a default or easily-hackable username and password. If an attacker took control of the thermostat of a warehouse, the attacker would have a great deal of leverage in asking for a ransom payment. As more devices become connected to the internet, they become more exposed to far-flung attackers.
How to Protect Yourself From Ransomware
Decryption tools are not available for most current strains of ransomware. Therefore, preventing it from getting a foothold is the best defense against it. Always use common sense, such as the following:
- Back up all files regularly so that recovering from any malware is easier.
- Update software routinely so that patches can prevent exploit kits from finding a way into your system.
- Never download attachments or click on links from unknown sources, no matter how official an email looks.
These three simple steps can save individuals and businesses from the monumental headache that ransomware causes.
2016 saw ransomware rise to become the most significant security threat in information technology. In 2017, we don’t expect that to change — but proper preparation can protect businesses and personal computer users from these serious threats.





