 Locky is a relatively new ransomware variant that can prevent access to files on your computer, locking them away with advanced encryption. If you have been victimized by this malicious software, Datarecovery.com can help. As leading security specialists, we can help you create an appropriate plan for preventing the spread of the malware while restoring the affected files.
Locky is a relatively new ransomware variant that can prevent access to files on your computer, locking them away with advanced encryption. If you have been victimized by this malicious software, Datarecovery.com can help. As leading security specialists, we can help you create an appropriate plan for preventing the spread of the malware while restoring the affected files.
We will attempt to find a decryption method, search for alternative methods of data recovery, and help you make a full recovery plan. We offer services for all ransomware victims. For more information, call 1-800-237-4200.
What is Locky Ransomware (And How Does It Work)?
Locky is a ransomware that was likely created by Dridex, a group of malicious hackers. Like other types of ransomware, it encrypts files on your computer and asks you to pay a fee in order to regain access to those files.
Here are a few important notes to keep in mind:
- Locky affects all devices attached to your computer, not just your primary hard drive.
- It can easily spread through a work network if not treated quickly. It can do more damage if your account has administrator access.
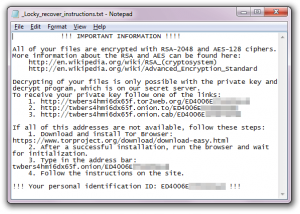
- When files are encrypted, they are completely unusable. Locky directs users to a darkweb site, accessible through a Tor browser; this site provides further instructions for paying the ransom.
- It affects Windows Volume Snapshot Service (VSS) files, so you cannot simply restore from an earlier automatic backup.
Because Locky uses both RSA and AES algorithms to encrypt data, it is thought to be unbreakable without access to the decryption keys. There do not appear to be exploitable patterns in the code. However, our specialists are looking into new decryption methods (see the last section of this page).
How Does Locky Ransomware Infect My System?
Locky is usually carried on a spam email that apparently has a Word document attachment. This attachment is actually a macro that installs the malware on the affected device.
The malware often presents itself as an invoice. You may receive an email with a subject line referencing an invoice number; a Microsoft Word document is attached. When you open up the document, it will display this message:
“Enable macro if the data encoding is incorrect.”
This is followed by a random set of characters and icons. Do not enable macros. Enabling macros will allow the program to begin encrypting key data on your computer.
 Locky targets specific file extensions, including images, Microsoft Office documents, databases, and bitcoin wallets. When files are encrypted, their extensions will change to .locky. This is where the ransomware gets its name. UPDATE: We’ve also learned of a new Locky variant named Zepto that appears to be very similar, and it changes file extensions to .zepto.
Locky targets specific file extensions, including images, Microsoft Office documents, databases, and bitcoin wallets. When files are encrypted, their extensions will change to .locky. This is where the ransomware gets its name. UPDATE: We’ve also learned of a new Locky variant named Zepto that appears to be very similar, and it changes file extensions to .zepto.
The rest of the filename is also changed, preventing users from targeting individual files for decryption efforts. The first 16 digits of the new filename is a unique ID to identify the victim. The next characters are the unique ID of the file.
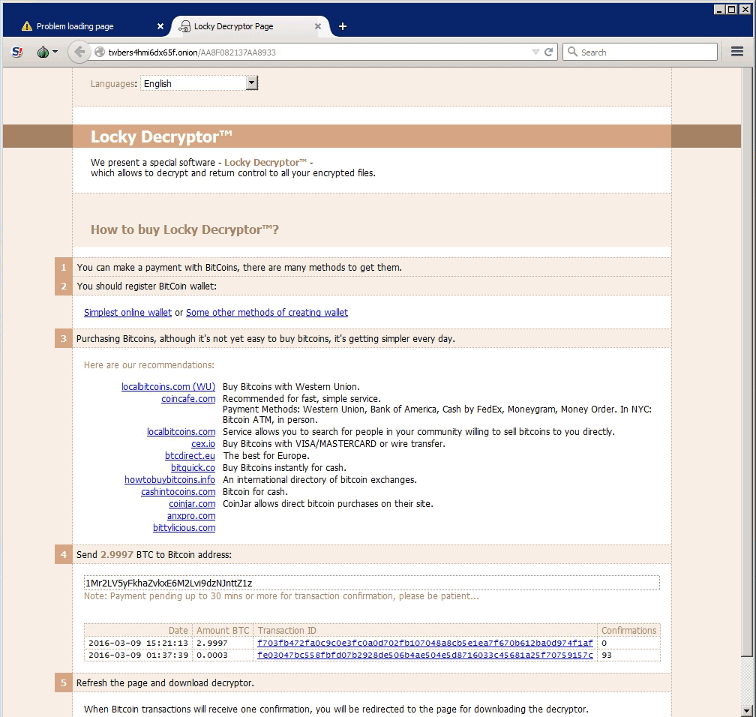
What Ransom Payment Does Locky Demand for Decrypting Files?
 Locky demands 1 to 5 bitcoins as a ransom. At the time that this article was written, that would mean a ransom of anywhere from $400 to $2,500 USD. If the user pays this ransom, installs a private web browser, and downloads and runs a special decryption program from the “darkweb”, the files are decrypted. Some variants may offer access to one or two files as proof that the decryption works.
Locky demands 1 to 5 bitcoins as a ransom. At the time that this article was written, that would mean a ransom of anywhere from $400 to $2,500 USD. If the user pays this ransom, installs a private web browser, and downloads and runs a special decryption program from the “darkweb”, the files are decrypted. Some variants may offer access to one or two files as proof that the decryption works.
In order to pay the ransom, users must purchase bitcoin, an untraceable currency. This ensures that the programmers behind Locky will not be caught.
The ransom message is displayed as an image file and a text file. The malware might set your desktop background to this image:
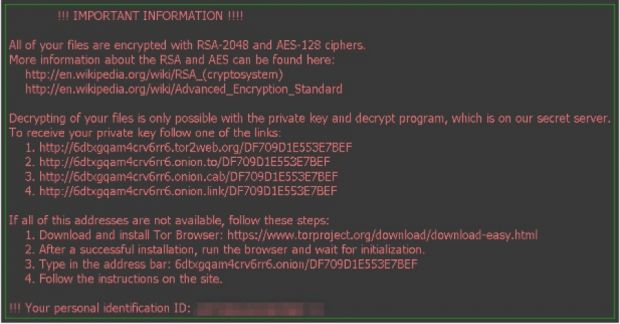
Can I Disable Locky Ransomware Encryption?
Whitehat hackers recently broke into the Locky command and control (C&C) servers, temporarily replacing the ransomware program’s messages with the phrase “Stupid Locky.” Hopefully, this will lead to new information that will allow security experts to create decryption tools. As of when this article was written (5/9/2016), full decryption tools are not yet available for this ransomware.
However, Datarecovery.com will continue to research potential methods of decryption in light of these recent developments. We encourage you to call our malware experts to discuss options.
Our primary goal is to restore data and eliminate malware without paying ransomware developers, but in extreme cases, we can help you organize safe, one-time payments to restore files safely and effectively.
Because of the nature of ransomware, we recommend seeking immediate assistance. You should disconnect the affected computer from the Internet to avoid spreading the malware. If you do not need to decrypt the affected device, you can safely format it to destroy all of the encrypted data. If you do need access to encrypted files, contact us today at 1-800-237-4200 for more information or to discuss your options.