Locky ransomware first appeared in February 2016 using a simple but ingenious social engineering method. The distributors sent thousands of emails around the world with an infected Microsoft Word document that appeared as gibberish when opened.
The message, “Enable macro if the data encoding is incorrect,” would prod users into changing their settings. Those who turned on macros in Word initiated the ransomware’s installation process and became the first victims of Locky.
Since that first wave of infections, Locky has vanished and then reappeared repeatedly. The one constant is that it always returns with a new extension and a few tweaks to better evade antivirus software.
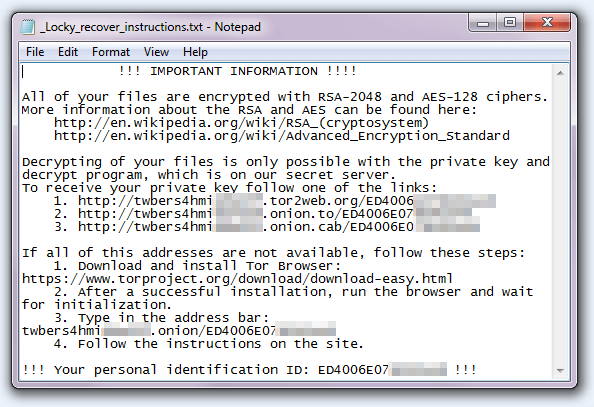
A previous Locky version ransom message
Ykcol Variant Uses 7z or 7zip Extension
The latest incarnation of Locky is the ykcol variant (for those wondering about the unusual name, ykcol is locky backwards). More significant than the updated extension is an updated tactic. This variant is distributed in a 7z file.
This file extension is probably unfamiliar to less techy computer users—it’s a format for highly compressed and encrypted files. Most computer users don’t even have the necessary software for unzipping such a file. Experts believe that the distributors hid the Locky variant in the obscure format to evade the filters of Gmail and other mail providers.
Ykcol Is the Latest in a String of Variants
From February 2016 to September 2017, Locky has morphed its .locky extension to .zepto, .odin, .shit, .thor, .aesir, .zzzzz, .osiris, .loptr, .diablo6, .lukitus, and finally, to .ykcol. None of these variants can be decrypted without the key, which only the distributors of the ransomware hold.
Locky has been a persistent threat over the last 18 months accounting for 14 percent of all ransomware detections globally in fall of 2016. It has since overtaken Cerber as the largest ransomware family. At times, the prolific ransomware appears to become inactive, but time and time again, it has reappeared with new features and distribution tactics.
Who Created Locky?
There are numerous clues, but no firm answers as to who created Locky. The ransomware has a flag that detects if a computer’s operating system uses the Russian language. If the OS is in Russian, Locky and its variants will not infect the computer. On top of that evidence, the majority of the ransomware’s attacks have been traced to Russia.
Though experts believe that a Russian group is responsible for creating and distributing Locky, it’s unclear exactly who they are. Locky is one of the most sophisticated ransomware families, so its creators are certainly highly skilled.
Attacks Continue at Huge Volumes
In early September 2017, security experts at Appriver detected 23 million spam messages containing Locky in a single 24-hour period. Clearly, the distributors are playing a numbers game. If only a miniscule fraction of those targeted download the ransomware, there will still be plenty of victims and potential ransom payments.
The subject lines of the spam emails contained words like “please print,” “documents,” or “photos.” The attackers attempt to lure in victims with curiosity over what may be attached to the email. Because of the overwhelming number of spam emails sent, it is more important than ever to scrutinize and verify attachments before downloading them.
Other security measures to avoid Locky and other ransomware include:
- Back up essential files frequently.
- Patch all software when updates become available.
- Use security software that detects ransomware behavior.
- Enable extension viewing so you can see executable files hidden as other documents.
Locky continues to evolve and other families of ransomware pose new threats every day. Use good internet hygiene and follow the above tips to avoid the costly effects of a ransomware infection.





