 CryptoLocker is one of the most successful pieces of ransomware ever introduced, and by conservative estimates, it has caused hundreds of millions of dollars in data loss. It installs through an infected email attachment, then holds the victim’s files hostage by encrypting them.
CryptoLocker is one of the most successful pieces of ransomware ever introduced, and by conservative estimates, it has caused hundreds of millions of dollars in data loss. It installs through an infected email attachment, then holds the victim’s files hostage by encrypting them.
Fortunately, Datarecovery.com offers CryptoLocker infection removal services for all types of systems. We can help you evaluate options and make a plan to restore your files quickly, safely, and with absolute security. Call us now at 1-800-237-4200 to speak with an expert.
What is CryptoLocker Ransomware (And How Does It Work)?
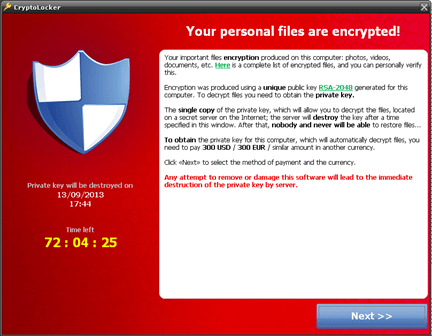
CryptoLocker is a ransomware program that prevents a victim from accessing key files by encrypting them. The encryption cannot be broken through standard brute force attacks, and victims must pay a ransom (usually $400) to restore the files to their original state.
Key attributes of CryptoLocker include:
- Unlike many ransomware programs, CryptoLocker has a time limit; the makers claim that if the victim doesn’t pay the ransom within a certain time frame, the private key that would allow for a successful decryption will be destroyed. Alternately, the ransom would increase the longer the victim waited to pay.
- This may be why so many people decided to pay the ransom; one study found that 3 percent of victims elected to pay to restore their encrypted files. This is a relatively high rate for ransomware.
- Many antivirus programs were unable to detect CryptoLocker until it had been installed owing to its unique method of installation.
Because CryptoLocker was successful, many malware creators have made clones. These do not necessarily have anything in common with the original CryptoLocker, except that they demand a ransom from their victims.
How Does CryptoLocker Ransomware Infect My System?
The original version of CryptoLocker spread through email. The victim would receive a message with a ZIP or RAR attachment; the message would appear to be legitimate, as it was often apparently sent from a reputable email address.
The archive would contain an executable file disguised as a PDF document. This file would add a key to the registry of the Windows computer and contact a command-and-control server to request a public key, created with 2048-bit RSA encryption. The server would also generate the private key; both keys are necessary to decrypt files.
CryptoLocker would encrypt a variety of files across all storage media and mapped network drives associated with the infected system. The malware chooses which files to encrypt by looking at file extensions. It also creates a log of each encrypted file on the registry key HKEY_CURRENT_USERSoftwareCryptoLockerFiles.
The affected extensions include:
3FR, ACCDB, AI, ARW, BAY, CDR, CER, CR2, CRT, CRW, DBF, DCR, DER, DNG, DOC, DOCM, DOCX, DXF, DXG, EPS, ERF, INDD, JPE, JPG, KDC, MDB, MDF, MEF, MRW, NEF, NRW, ODB, ODC, ODM, ODP, ODS, ORF, P12, P7B, P7C, PDD, PEF, PEM, PFX, PPTM, PPTX, PSD, PST, PTX, R3D, RAF, RAW, RTF, RW2, RWL, SR2, SRF, SRW, WB2, WPD, X3F, XLK, XLS, XLSB, XLSM, XLSX
Some CryptoLocker clones may target different files than the extensions listed above. If you believe that your system is infected with CryptoLocker, we strongly recommend turning off the device and seeking a professional evaluation before taking any other steps.
What Ransom Payment Does CryptoLocker Demand for Decrypting Files?
Some versions of CryptoLocker set a ransom by analyzing the number of encrypted files, so there was not a standard ransom. However, early versions asked for an initial ransom of $400 USD.
However, as mentioned earlier, ransoms could gradually increase over time. Some users reported ransoms of 10 bitcoin or more.
As is the case with most ransomware, CryptoLocker demanded bitcoin as payment, since bitcoin is essentially untraceable.
Can I Disable CryptoLocker Ransomware Encryption?
Authorities were able to successfully shut down the original CryptoLocker servers, and decryption tools are available for files encrypted by the first version of the malware. However, the initial success of CryptoLocker resulted in the release of a number of clone programs that use a similar ransom request to extort money from victims. Many of these programs use the name CryptoLocker, but they share few characteristics with the original.
One of the most common malware distributions bearing the CryptoLocker name is TorrentLocker. This program is not made by the creators of CryptoLocker, and infections need to be approached differently. This can cause confusion for ransomware victims, which is why we will provide an evaluation and recovery action plan at the outset of our services.
Datarecovery.com will help you decrypt files, prevent the ransomware infection from spreading, and as a last resort, organize a secure, private payment to restore access to affected files. Our primary goal is to return your data without rewarding the creators of these malicious programs.
Get started today by contacting our security specialists and asking about CryptoLocker ransomware recovery. Call 1-800-237-4200 to get started.




