 Cerber ransomware is a quickly evolving type of malware that encrypts files on a computer so that they are unreadable. The attackers then demand a ransom to decrypt the files.
Cerber ransomware is a quickly evolving type of malware that encrypts files on a computer so that they are unreadable. The attackers then demand a ransom to decrypt the files.
If Cerber has infected your computer, turn it off, disconnect all media from it, and call Datarecovery.com at 1-800-237-4200. Our malware experts can assess your situation and begin a plan to restore your files.
What is Cerber Ransomware (And How Does It Work)?
Cerber is a type of malware called crypto-ransomware. Attackers find a way to gain entrance to a victim’s computer, and then Cerber encrypts the files on that computer. Encryption is normally used for keeping the information in files secret, but when crypto-ransomware encrypts files, the goal is to withhold the information from the rightful owner until a ransom is paid.
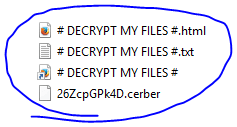 After Cerber has encrypted all of the files it can and renamed them to unrecognizable names often with extension “.cerber”, it puts a note for the victim on the computer desktop. It also creates several ransom note files. These include a text file, HTML file, and a VBS (Visual Basic Script), usually named like “# DECRYPT MY FILES #”. The messages direct the victim on how to pay the ransom, which generally starts at 1.24 bitcoins ($917 at the time of writing).
After Cerber has encrypted all of the files it can and renamed them to unrecognizable names often with extension “.cerber”, it puts a note for the victim on the computer desktop. It also creates several ransom note files. These include a text file, HTML file, and a VBS (Visual Basic Script), usually named like “# DECRYPT MY FILES #”. The messages direct the victim on how to pay the ransom, which generally starts at 1.24 bitcoins ($917 at the time of writing).
Notable Features of Cerber Ransomware Include:
- The ransom doubles from 1.24 to 2.48 bitcoins after seven days of nonpayment.
- Attackers can buy Cerber from underground Russian forums, which makes ransomware attacks possible from anyone with enough money to pay.
- In July of 2016 alone, victims paid $195,000 to Cerber assailants in order to decrypt encrypted files.
- Cerber has targeted more than 150,000 computer users, including both individuals and businesses, in July of 2016 with no signs of slowing.
- Cerber favors targeting businesses over individuals because of the malware’s ability to encrypt databases and mapped or unmapped network shares. This can cripple businesses.
- When Cerber initiates, it first checks a victim’s computer to see if they are from a variety of former-Soviet republics. If the computer is from any of these countries, the ransomware terminates and does not infect the computer.
Security experts have cracked the earliest version of Cerber, but the developers have already responded by updating the malware to an as-yet unbreakable version. Retrieving backup copies of data is more feasible than decrypting files for the later versions of Cerber.
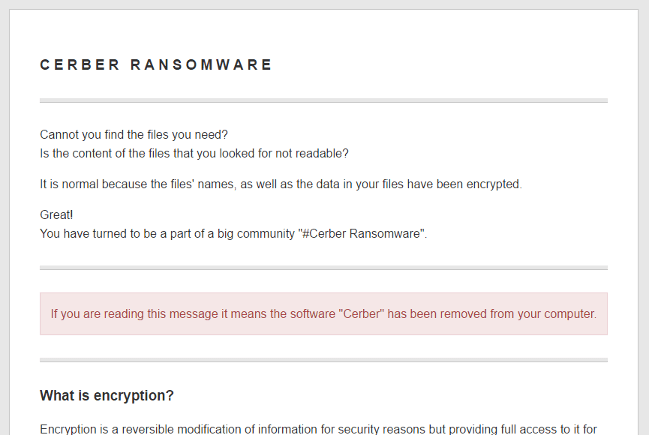
View the full ransom note screenshot here
How Does Cerber Ransomware Infect My System?
Cerber infects a computer when the user clicks on a malvertisement, or malicious advertisement. Malvertisements are the preferred way for criminals to attack computers. Criminals can place legitimate advertisements on a website until the site trusts them, and then they place an ad that is capable of hijacking a computer when someone clicks on it.
The compromised advertisements are made to look as innocuous and legitimate as possible. However, once someone clicks on one of them, the visitor can be tricked into downloading the payload. After Cerber encrypts all of the files it can, it leaves a note with instructions on how to pay the ransom.
Paying the ransom and decrypting the data is a convoluted and uncertain process. It involves temporary web pages that go offline after a short period, installation of the Tor Browser, .onion sites (also temporary) on the Tor anonymous network, crypto-coin wallet management and exchange transactions, and of course executing the decryption process with the unique decryptor. Worst of all, there is no guarantee that the attackers will provide a working decryptor software once the ransom is paid. Even when cyber-criminals attempt to send a working decryptor, there can be technical difficulties that leave the victim out of money and without their files. One common example we’ve seen is two different intances of the ransomware software having run independently and caused overlapped encryption.
Can I Disable or Remove Cerber Ransomware Encryption?
As with all malware, prevention is the best defense. However, if Cerber has already infected your machine, recovering files from alternate sources is preferable to decrypting the files. An early version of Cerber has been cracked, but the developers continue to update the malware and later versions have proved tougher to break.
If you believe that Cerber has infected your computer, remember that consulting professionals quickly is in your best interest. Datarecovery.com can help you determine if you have backup copies of your files and determine the best way to recover them.
Call 1-800-237-4200 to start the process of restoring your unreadable files. Our malware experts will analyze your situation and begin the process of recovering your information.





