Looking for something? Refine your search
- Categories
- Backup
- Cloud
- Computer Forensics
- Computing and CPU Power
- Cryptocurrency
- Damage
- Data Loss Prevention
- Data Recovery Knowledge
- Data Recovery News
- Data Recovery Service
- Data Types
- Database
- Digitization
- Encryption
- Flash Drive
- Hard Disk
- Investing and the Stock Market
- Mac/Apple
- Media
- Mobile Device
- NAS
- Network Security
- Office Documents
- Outreach
- Photos & Images
- RAID
- Ransomware Recovery
- Removable Media
- SAN
- Secure Deletion
- Server
- Services
- SSD
- Storage Industry
- Tape
- Uncategorized
- Video
- Tags
- actuator
- Apple
- backup
- bitcoin
- breach
- clean room
- clone
- computer forensics
- cryptocurrency
- cybercrime
- data recovery software
- data recovery tips
- decision tree
- EEPROM
- encryption
- ethereum
- exploit
- financial records
- fire damage
- flood
- guide
- hard drive data recovery
- hard drive failure
- hard drive manufacturers
- head ramps
- helium
- how to
- hurricane
- iOS
- landing zone
- leak
- Mac
- Mac OS
- machine learning
- macos
- Midwest
- migration
- music data recovery
- NAND
- NFT
- NVRAM
- operating system
- OS X
- parts
- password
- PCB
- Phoenix
- power surge
- RAID
- ransomware
- rebuilt
- SATA
- SaveMyFiles
- SSD
- statistics
- storms
- tornadoes
- TRIM
- video conversion
- virus
- water damage
- wildfires
- windows 10
- windows 10 guide
Europol: Ransomware-as-a-Service Operations Are Losing Users
Cybercriminals are moving away from popular ransomware-as-a-Service (RaaS) platforms thanks to major efforts from law enforcement agencies, per a recent threat assessment published by Europol. RaaS is a business model in which cybercriminals provide ransomware software and infrastructure to...
July 25, 2024
Don’t Use CHKDSK On a Failing Hard Drive
Recently, we searched for “failing hard drives” to see whether the internet was dispensing bad advice regarding drive failures (and to see if our name came up). Google’s experimental A.I. answered our question — and promptly provided instructions that could...
July 23, 2024
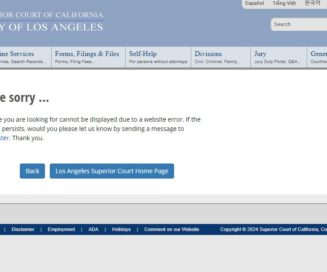
Ransomware Attack Forces Los Angeles County Courts to Close
The Los Angeles County Superior Court is reeling from a major ransomware attack, per an announcement from the L.A. County Sheriff’s Department. The attack has impacted the entirety of the Superior Court’s operations, essentially grinding its systems to a halt....
July 22, 2024
Sacramento Credit Union Announces Outage Due to Ransomware Attack
Patelco Credit Union, a Sacramento-based credit union with 37 local branches, has confirmed that its recent security breach occurred due to a ransomware attack. In an email sent to the members of the credit union, Patelco CEO Erin Mendez said...
July 2, 2024
Lockbit Ransomware Group Announces Breach of U.S. Federal Reserve
The Lockbit 3.0 ransomware group claims to have breached the United States Federal Reserve, exfiltrating about 33 terabytes of potentially sensitive data. The group claims that the stolen data includes “Americans’ banking secrets,” though they have not yet published any...
June 24, 2024
Ransomware Attack Causes Blood Shortages at London Hospitals
A ransomware attack targeting Synnovis, a U.K. healthcare partnership, has significantly disrupted medical procedures in several of London’s largest hospitals. The incident has prevented hospitals from matching patients’ blood types at a normal frequency. Surgeries and other procedures that require...
June 12, 2024
Ascension Confirms Ransomware Attack, Ongoing Recovery Efforts
Ascension, which operates 140 hospitals across the United States, has confirmed that an ongoing service outage was caused by a ransomware attack. The organization says that they have implemented procedures to “ensure patient care delivery continues to be safe and...
May 13, 2024
Before Recycling a Hard Drive, Read This
You should never toss a hard drive into a dumpster — hard drives are recyclable, and given that we create more than 59 million tons of electronic waste every year, every bit of recycling counts (pardon the pun). But while...
May 8, 2024
DragonForce Ransomware Group Posts Audio of Conversations with Victims
In an apparent attempt to compel their victim to pay up, the ransomware gang DragonForce has published a recording of a phone call with one of its victims’ employees. The recording was published on DragonForce’s dark web page. For ethical...
April 14, 2024
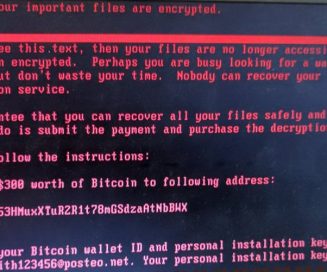
Should You Pay For Ransomware? Never — Here’s Why.
Ransomware payments reached an estimated $1.1 billion in 2023, per a report from crypto-tracing firm Chainalysis. It’s no wonder that ransomware is a growing threat — and from the victims’ perspective, the temptation to pay is certainly understandable. But...
April 10, 2024