Ransomware recovery services typically employ a multi-faceted approach to help organizations recover from ransomware attacks. Success is largely dependent on the type (or variant) of ransomware; in some cases, decryption is relatively easy, while in others, it’s practically impossible without direct access to the attacker’s systems.
At Datarecovery.com, we’ve invested heavily in ransomware research and development. Here’s a breakdown of the basic steps we use when approaching a ransomware data recovery case. To discuss ransomware remediation with an expert, call 1-800-237-4200 or submit a case online.
1. Threat identification and analysis.
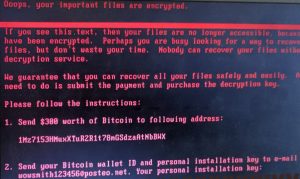
A screenshot of the Petya variant’s ransomware message.
The first step in ransomware recovery is identifying the specific type of ransomware used in the attack, as well as the extent of the attack.
In most instances, the ransomware variant can be identified easily — many ransom notes will explicitly state the (anonymized) name of the malware group, and some even describe the encryption methods used. However, other information about the malware can be useful in recovery and threat mitigation:
- Ransomware Behavior: Experts observe how the ransomware interacts with your system, including its encryption speed, targeted file types, and any other unique characteristics.
- Encryption Methods: Different ransomware strains use various encryption algorithms. Analyzing these methods helps determine the complexity of the attack and the potential for decryption.
- Ransom Notes and Communications: While we do not recommend paying ransoms (in part because it doesn’t restore data for about 25% of victims), ransom notes can provide helpful clues about the attacker’s level of sophistication.
- Forensic Investigation: Experts examine affected files, network logs, and system configurations to understand the attack’s scope, entry point, and overall damage.
In short, evaluating the ransomware will allow us to determine whether decryption can be completed within a reasonable timeframe. We also use the analysis to find interventions that may prevent future attacks.
2. Decryption attempts.
The goal of any ransomware recovery project is decryption. That’s not always possible — highly sophisticated ransomware gangs certainly exist — but a high percentage of bad actors make basic mistakes.
Ransomware experts may be able to take advantage of those mistakes. This means reverse engineering the ransomware to find appropriate methods of decryption.
We want to note here that public tools are available for ransomware decryption — as a member of the cybersecurity community, we support projects like No More Ransom, which houses ransomware removal tools and decryptors for fighting major ransomware variants. With that said, not every variant can be resolved with open source tools.
And even when open-source tools are available, professional ransomware experts can help organizations leverage those tools effectively (and prevent accidental data loss). Affected systems may need to be rebuilt from scratch, reinstalling operating systems, applications, and configurations. Experts can also identify and patch vulnerabilities.
3. “Reverse” social engineering.
If decryption proves impossible, recovery services may engage in “reverse” social engineering. It’s crucial to understand that paying a ransom can be illegal, so reputable recovery services do not negotiate ransom payments. For more information, read: Paying a Ransomware Ransom Is (Usually) Illegal.
Instead, recovery firms use reverse social engineering techniques to manipulate the attackers into providing a decryption solution without any financial transaction.
The goal is to outsmart the attackers and recover the data without supporting bad actors.These methods require a great deal of finesse and ethical consideration, and they’re not effective if cybercriminals are aware of them — so we’re not describing them in detail on this page.
4. Disaster recovery and threat mitigation.
Regardless of whether decryption or negotiation is successful, recovery services prioritize restoring your systems and preventing future attacks. This includes:
- Data Restoration: Recovery of data from clean backups, which may involve offline backups, cloud backups, or other secure solutions.
- System Rebuilding: Rebuilding affected systems from scratch, including reinstalling operating systems, applications, and configurations.
- Vulnerability Patching: Identifying and patching vulnerabilities that allowed the ransomware to infiltrate your network. This may involve updating software, configuring firewalls, and implementing security protocols.
- Security Enhancement: Implementing robust security measures like anti-ransomware software, penetration testing, and multi-factor authentication to prevent future attacks.
- Dark Web Monitoring: Continuously monitoring the dark web for any signs of compromised data related to your organization. This allows for quick action to mitigate damage if credentials or sensitive information are found to be leaked.
Like many types of data recovery services, ransomware recovery is best handled on a case-by-case basis — not all enterprises will need long-term dark web monitoring, and some may prefer to restore from backups rather than wait for a potential resolution through decryption.
As a world leader in ransomware remediation, Datarecovery.com offers comprehensive ransomware recovery services, including expert analysis, decryption attempts, secure data restoration, and proactive threat mitigation. Our “no data, no charge” guarantee ensures you only pay for successful file recovery.
To learn more, call 1-800-237-4200 to speak with a ransomware expert or submit a case online.





