
Locky is the common name for a ransomware variant that first appeared in 2016. The first version of Locky was distributed by the Necurs botnet; subsequent versions have been introduced by Necurs and other distribution groups.
Typically, the ransomware is activated when a victim opens a Microsoft Word document that appears to display gibberish. The user is instructed to “enable macro if data encoding is incorrect.” If the user enables macros, the ransomware is activated and encrypts files on the target computer, replacing their file extensions with the unusable “.locky” extension.
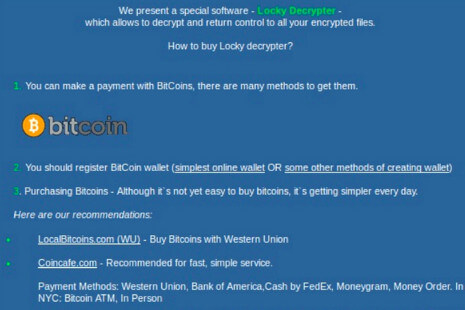
The victim is unable to access their files unless they pay the ransom in bitcoin. Locky creates text files and images with instructions for paying the ransom.
While the original version of Locky was disabled temporarily by white-hat hackers, malware groups quickly created similar variants such as PowerLocky (discussed below). In addition to the “.locky” file extension, Locky variants may change the file extensions of targeted files to:
- .aesir

- .asasin
- .diablo6
- .odin
- .thor
- .ykol
- .zepto
- .zzzzz
This is a partial list of possible .Locky file extensions. To accurately diagnose a Locky infection, we recommend contacting a ransomware recovery professional.
For more detailed information about the original version of Locky, read: Locky Ransomware Infection And Decryption Services. The linked page was written in May 2016, and some information may be outdated.
How Do I Prevent a Locky Ransomware Infection?
The simplest way to prevent a Locky ransomware infection is to avoid opening Microsoft Word documents from unrecognized sources. However, Locky can also “spoof” email accounts from known users — avoid enabling macros on any Microsoft Word document unless you’re able to fully verify the purpose of the macros.
Some versions of Locky utilize known exploits; these variants do not rely on Microsoft Word macros to activate. In other words, when the user downloads the file and attempts to open it, the ransomware will immediately begin encrypting targeted data.
For enterprises, software is available to quarantine Locky files and prevent them from infecting networks. However, malicious attackers frequently update their attack vectors, so keep a backup of important systems (preferably an air-gapped backup that isn’t connected to the network).
Is There a Locky Ransomware Decryption Tool?
Because several ransomware variants share the characteristics of the original Locky malware, there’s no simple answer here. One version, PowerLocky, has a free decryption program created by programmer Michael Gillespie. Learn more about PowerLocky Decrypter here.
However, some variants that utilize the same attack vectors as PowerLocky use more robust methods. The classic Locky ransomware (and many subsequent versions) used server-side key generation, which made manual decryption virtually impossible. Additionally, some larger files such as databases may still be unusable after decryption with free tools due to file corruption that occurs during the decryption process.
Because many ransomware variants are designed to spread quickly, the safest course of action is to disconnect the infected system from any networks as quickly as possible. If you attempt decryption using free tools, make sure you’re accessing the infected device with a computer that contains no other sensitive data.
Is Data Recovery Possible for Computers Infected with Locky?
In most cases, ransomware recovery is possible for Locky infections. We recommend contacting a professional data recovery provider as a first course of action — preferably, before attempting decryption on your own, since some free decryption tools may cause corruption for certain types of files (such as databases and email archives).
To discuss options for recovering from a Locky ransomware infection, contact us today at 1-800-237-4200 or click here to start a case online.





